In order to request and manage certificates in Java, we will use the Java keytool. This is a key and management utility supplied with the JDK.
The Java KeyTool is a command line utility with various options.
The first option required is the -genkey option.
This will add the private key to an existing keystore; or, if the keystore specified does not exist, will create a new one.
To create a new keystore, you use the following command (without any line break) at the command prompt:
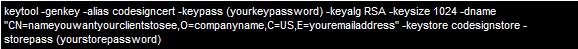
Note: When you run this command, it produces no output:
This command will create a keystore named "codesignstore".
The alias is the unique identifier of this entry. Whilst the key will include the following information: CN= should be the name you want your customers/clients to see when they open your application O= your company name C= your two digit country code E= your email address
Note: It may be a good idea to note the keystore and key passwords. These will be required later during the installation procedure.
Certificate Signing Request (CSR) Generation
The next step is to generate a Certificate Signing Request (CSR). To do so, use the following command:
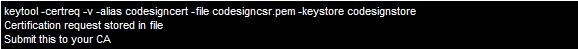
You will now find a file called codesigncsr.pem in the your working directory. It will look something like this:
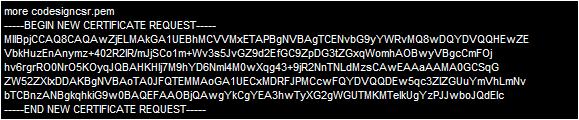
This file is what you submit in the GlobalSign ObjectSign Java certificate request application for signing.
After verification, GlobalSign will send you an email with your certificate included as an attachment (eg. cert123.pem). You can rename this file to something more obvious like: javacodesigncert.pem
Opening this in a text editor will display something like:
-----BEGIN CERTIFICATE-----
MIIDJjCCAtCgAwIBAgIQVd1yrfv2854JsDjU08ZA+DANBgkqhkiG9w0BAQUFADCB
qTEWMBQGA1UEChMNVmVyaVNpZ24sIEluYzFHMEUGA1UECxM+d3d3LnZlcmlzaWdu
LmNvbS9yZXBvc2l0b3J5L1Rlc3RDUFMgSW5jb3JwLiBCeSBSZWYuIExpYWIuIExU
RC4xRjBEBgNVBAsTPUZvciBWZXJpU2lnbiBhdXRob3JpemVkIHRlc3Rpbmcgb25s
eS4gTm8gYXNzdXJhbmNlcyAoQylWUzE5OTcwHhcNMDUwMzA1MDAwMDAwWhcNMDUw
-----END CERTIFICATE-----
You can also see the file contents using KeyTool with the following command:
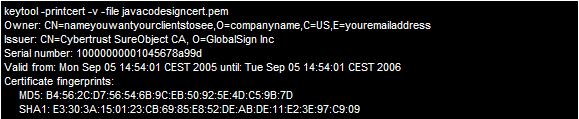
Certificate Installation Procedure
We are now ready to build the keystore: You will need the following two Cybertrust CA certificates in order to have your certificate trusted and able to sign:
The first step is to import the GTE CyberTrust Global Root and the Cybertrust SureObject CA just mentioned, using the following two commands (your browser may rename these files, you can manually change them back to ct_root.cer and sureobject.cer or change their names in the commands below):
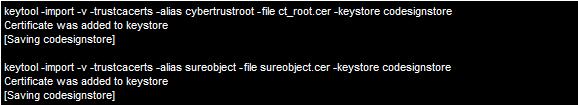
These messages indicate that the certificates were imported successfully.
Remember to give each certificate a unique alias.
Next, verify the contents of the keystore again:
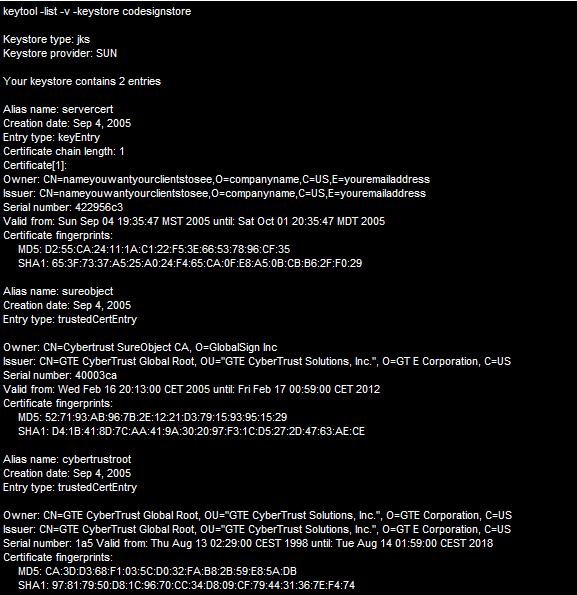
The keystore now has the private key and the root certificates. We can now import the code signing certificate.
To do this, we use the import command again, but drop the –trustcacerts and –noprompt, and specify that the alias is the same as the private key alias.
Run this command only after you have imported the root certificate and any intermediate certificates.
Having these files available allows the keytool to properly chain your signed certificate to the proper root certificates.
Finally, running another listing of the keystore, the output should look like this:
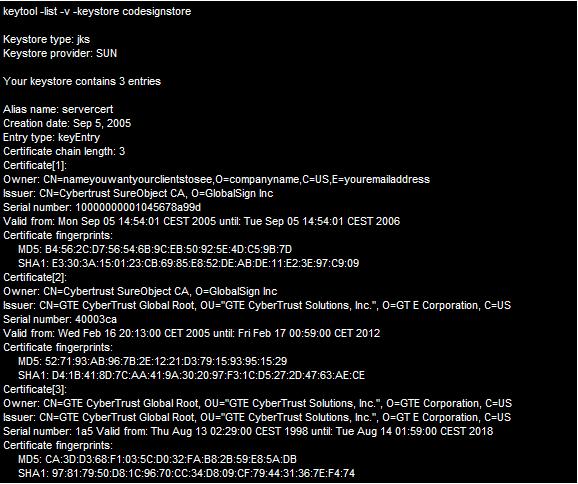
Here, the most important thing you want to see is under the private key alias. You should find:
Certificate chain length: 3
This tells you that keystore able to establish the certificate chain, and your keystore is ready for use.
Signing your Java Code
Now you will be able to sign your java code using the jarsigner utility. A typical commmand for this, using the above example, looks something like:

Further information on Java KeyTool and Certificate generation can be found on the Sun website. |